Eliminate East-West Traffic Hair-PinningEliminate East-West Traffic Hair-Pinning
Networks must be designed to take into account the additional (hair-pinned) traffic routed through an appliance-based firewall.
January 18, 2021

A firewall is a firewall, right? While on the surface that assumption may appear to be correct, a closer look reveals that there are critical differences between a traditional, appliance-based firewall that protects your network perimeter and a distributed, scale-out internal firewall that protects east-west traffic within your data center.
It’s true that both types of firewalls monitor network traffic, detect threats, and block malicious activity. However, appliance-based firewalls are designed to monitor north-south traffic, which has different volumes and characteristics than east-west traffic. Traditional north-south firewalls were never designed to be used interchangeably to protect both north-south and east-west traffic.
VMware East-West.jpg
While it might appear to be the right choice, provisioning appliance-based firewalls for east-west traffic monitoring is not only expensive. It's highly ineffective in delivering the level of control and performance required to protect growing numbers of dynamic workloads.
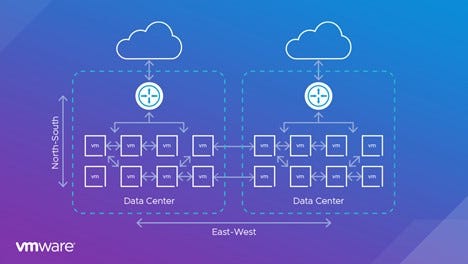
Creating Traffic Jams During Volume Spikes
One of the most common drawbacks of using appliance-based firewalls as internal firewalls is the need to hair-pin east-west traffic to and from the appliance.
A VMware customer recently experienced this firsthand. As a global telecommunications company with hundreds of millions of users in more than a dozen countries, the organization wanted to protect business-critical, consumer-facing mobile application infrastructure. To do so, it needed to segment and secure large amounts of network traffic on in-house infrastructure using an internal firewall approach. The telecom decided to deploy a hardware-based firewall as its internal firewall solution.
It didn’t take long for the company to begin experiencing performance issues. The appliance-based solution could not scale to protect all the workloads and traffic across the telecom’s dev/test, production, and DMZ zones. Because the traffic was hair–pinned to and from the firewall appliances, the company experienced performance problems during traffic spikes when new versions of the application were released.
Pinning Down the Problem
Why is hair-pinning a problem for east-west traffic? When a perimeter firewall is used as an internal firewall, traffic is forced to and from a centralized appliance. This creates a hair-pin pattern, which consumes an inordinate amount of network resources and limits scalability. That's why, despite deploying more than 200 firewall appliances, the telecom customer repeatedly encountered performance bottlenecks whenever there was a sudden increase in traffic.
In addition to increasing latency, hair-pinning east-west traffic adds complexity, both from a network design and an operations perspective. Networks must be designed to take into account the additional (hair-pinned) traffic routed through an appliance-based firewall. From the operational side, the security operations team must adhere to the network design and be aware of its constraints when sending additional traffic for inspection to the firewall.
Hair-pinning and ensuring performance limitations are some of the reasons why most organizations that use appliance-based firewalls to monitor east-west traffic do not inspect most of it—they're forced to choose performance over security.
Turning to a Distributed Internal Firewall
A distributed, scale-out internal firewall is different. First, it is purpose-built for monitoring large volumes of east-west traffic without creating a single choke point. With a distributed internal firewall, there's no need to hair-pin traffic, which eliminates the complexity and latency issues involved in using appliance-based firewalls to monitor the internal network.
A distributed firewall that is intrinsic to the infrastructure moves enforcement to where the data is, rather than the other way around, enabling organizations to secure all east-west traffic—not just selected workloads—while minimizing the impact on network and server infrastructure.
That’s why the telecom company we mentioned earlier is replacing its hundreds of firewall appliances with VMware NSX Service-defined Firewall, giving the business a single firewall model and management console for its entire infrastructure. VMware simplifies operations for the company and eliminates hair-pinning of the telecom’s east-west traffic. Performance bottlenecks disappear—even as traffic volume and workloads grow.
What’s Required for an Internal Firewall?
To protect large volumes of east-west traffic without sacrificing security coverage, network performance, or operational agility, an internal firewall must be able to do more than avoid hair-pinning traffic. The right internal firewall solution must support the following five critical requirements:
Distributed and granular enforcement of security policies
Scalability and throughput to handle large volumes of traffic without impeding performance
Low impact on network and server infrastructure
Intra-application visibility
Workload mobility and automatic policy management
For all these reasons, not all firewalls are the same when it comes to fulfilling the requirements of monitoring and protecting east-west traffic.
Because an appliance-based firewall is designed for the unique use case of securing the perimeter, it can’t deliver on the critical requirements for protecting traffic within the data center. Attempting to use it for internal firewalling means incurring exceptionally high costs and complexity while accepting far too many security compromises.
A distributed internal firewall, however, supports all of the above requirements while enabling your company to mitigate security risk, ensure compliance, accelerate security operations, and simplify your security architecture.
Helpful Resources
Learn more about the differences between appliance-based firewalls and distributed internal firewalls in our white paper “Five Critical Requirements for Internal Firewalling in the Data Center.”
Read more about:
Data center modernizationAbout the Author
You May Also Like




