We Need to Talk About the Security Posture of Your Network OperationsWe Need to Talk About the Security Posture of Your Network Operations
Enterprises need to understand that protecting their operational APIs is important to the future of your enterprise security posture. That is particularly true for an operational API that directly impacts the network.
August 29, 2024

I know you just got in, and it's late, but we need to have a talk. You know, that talk. You see, I noticed that your network operations are increasingly automated, according to the latest analysis of our annual research. Here’s a chart to prove that out.
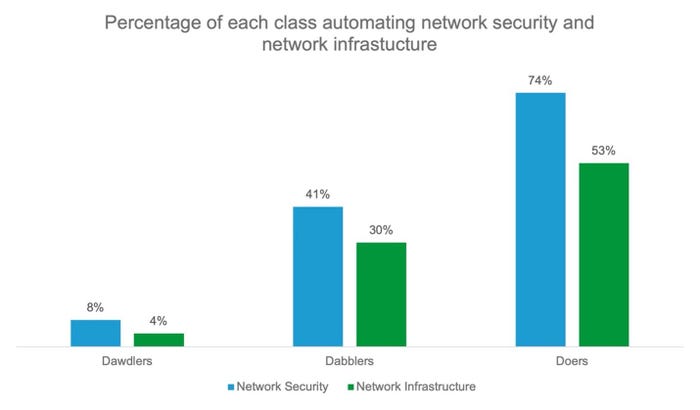
I’m not surprised by this at all. As an organization progresses on its digital transformation journey, it matures in each of six key technical domains. One of them is, of course, the network. Part of that maturation process involves automation, which I notice you are doing more of. Don't deny it; I looked in your network closet.
Security Posture Key Elements: Automation and APIs
So, here’s the thing I’m worried about—the security of the APIs you’re using to automate.
As you automate more and more, you’re not just using scripts that are initiated by human beings. You’re starting to pass that responsibility on to systems. Systems that are AI-driven. A significant percentage of the most digitally mature organizations—that’s dabblers and doers in our lingo—have systems that execute scripts based on conditions to make minor configuration changes and push policies that adjust delivery and security services.
And I suspect you’ve at least tried it, too.
I’m not surprised. After all, your peers are excited about this capability, with the use of generative AI to adjust policies for both application delivery and security receiving top billing on the list of ways to use AI in IT in our research.
I don’t want to stop you, but I do want to caution you about safety. Yes, it’s that talk, after all. I need you to think about the APIs that are being used to make these changes—sometimes automatically—and whether they’re properly protected against bad actors, both those on the inside and outside.
Because we did some more research and, well, it’s not looking good. I’m worried about your operational security posture. Most organizations (over 65%) are automating operational workflows and using APIs to do it. But most of your peers aren’t applying any security to those workflows.
I know, I know. You probably didn't think about that. That's okay; that's why we're talking today.
You see, the more you rely on any system to perform critical tasks, the more attention to security will be needed. Access control, of course, but also the same kind of checks you do on other APIs to keep them safe. Checks for malicious content, protocol abuse, and odd behaviors that may be indicative that something other than a known system or human being is invoking those APIs.
A CISO cyber resilience report out of the UK earlier this year found that 72% of CISOs claim remote working has complicated their organization’s cyber resilience posture. And while I’m all in favor of remote working—having done it since the turn of the century—I can’t disagree with this finding now that I know how little attention is being paid to protecting the operational APIs that drive the business.
It's late now, and I stayed up to have this talk with you because I thought it was important for you to understand that protecting your operational APIs is important to the future of your enterprise security posture. So please, at least think about the consequences of someone exploiting an operational API that directly impacts the network.
About the Author
You May Also Like




