How to Secure Access Switch PortsHow to Secure Access Switch Ports
Follow these steps to protect your network from unauthorized users and devices.
May 12, 2016


port security basics.jpg
One of the easiest ways to secure a network is to make sure you have some simple security features enabled on switch ports to which your end users connect. Properly securing switch access ports is fairly straightforward, but some techniques are often overlooked. In this guide, I'll discuss a few ways to protect your network by restricting access to users and devices you want connected to your access switches. Most enterprise-class switches have identical or similar port security features. So while the examples in this guide uses a Cisco switch, switches from other vendors can be configured in a similar manner.
One general bit of advice regarding the configuration of switch ports and VLANs on a production network: The default VLAN 1 should not be used for data transport. There are several reasons for this, but the primary reason is that VLAN 1 was meant to transport switch management communications between devices such as CDP, PAgP and VTP. I recommend this communication be separated from any user data running across the switch.
In this guide, I'll describe four different access-port configuration options to show how they provide added security benefits, and explain how to configure them. While these configurations don’t guarantee that your network will be completely safe from malicious or unauthorized behavior at the access-layer, they certainly help close some common security gaps. The concepts I'll cover are:
The purpose for configuring access-only switch ports
Why enabling BPDU guard will protect against unauthorized network devices
How port security can restrict unauthorized end devices
How to handle unused switch ports
Let’s get started.
NEXT PAGE: Access-only switch ports
(Image: D3Damon/iStockphoto)
The purpose for configuring access-only switch ports
By default, access switch ports are in a dynamic-desirable mode. What this means is that it essentially listens to devices to connect to it, and then either becomes an access port or a trunk port depending on the messages it receives from the neighboring device or switch. If the switch port is intended to only allow end devices and not switches, I strongly advise configuring the port specifically as an access-only port. That way, if a switch is either intentionally or unintentionally connected to that port, it cannot build a trunk that transports multiple VLANs. Only one VLAN is allowed to be configured on an access port.
The one caveat is the ability to configure both a data and a voice VLAN. This scenario involves an IP phone connecting to the switch first, then the phone connecting to a PC. Typically voice VLANs are separate from data VLANs and the access mode allows for this.
In the example below, I configure two VLANs. VLAN 15 is our data VLAN and VLAN 25 is our voice VLAN. I then configure port 1/0/10 as an access-only port and configure the data and voice VLANs accordingly.
switchport-mode-access.png
Why enabling BPDU guard will protect against unauthorized network devices
Bridge Protocol Data Units (BPDUs) are messages exchanged between switches that communicate and negotiate Spanning Tree Protocol (STP) settings. If the ports you are configuring should never have another switch attached to them, it's beneficial to enable BPDU guard. If a switch is connected to a port that is configured for BPDU guard, as soon as BPDUs are seen on the interface, the port is shut down and placed into an error-disable mode. Not only does this prevent unauthorized network devices from connecting, it also prevents the possibility of an STP loop, which can severely impact data transport for data communications. The example below shows how to enable BPDU guard on port 1/0/10.
bpdu-guard.png
NEXT PAGE: Restricting unauthorized devices
How port security can restrict unauthorized end devices
While it can become a bit cumbersome to manage port security on all access ports, using it on switch ports that are easier to access -- such as in lobbies and meeting rooms -- is a good idea. One of the purposes of port security is to restrict input to an Ethernet switchport by identifying and statically assigning the MAC address of an end device or devices to a specific switchport. Only the device with that MAC address is allowed to transmit data onto the network.
An alternate method is to put the switch port into "sticky" mode, allowing it to learn and remember the MAC address of the first device connected to the port. That MAC address is then saved to the running configuration and treated as a static MAC address assignment from that point on.
If an unknown device attempts to connect and is in violation of the port security settings, the switch can be configured to either shut down the port completely by placing it into error-disable mode or simply restrict the foreign device from transmitting/receiving data and generate an SNMP trap message to alert administrators of the security violation. Note that if you choose to completely disable the port, you can configure the switch to automatically re-enable it by using the errdisable recovery interval command. The timer to re-enable the port is configurable; if you don't specify a time in seconds, the timer defaults to 300 seconds (5 minutes).
In this example, I configure port security on access port 1/0/13 to dynamically learn and remember the first three MAC addresses that connect and only allow those devices to communicate (sticky mode). If a foreign device connects at a later time, the switch port will shut down and be placed into error-disable mode for 15 minutes.
port-sec-config.png
We can then verify the port security on our port by issuing the show port-security command as shown here:
port-sec-show.png
Keep in mind that MAC addresses can be spoofed by technical users, so it's not a foolproof method. But for most cases, the deterrent is more than sufficient for preventing unauthorized network access.
NEXT Page: Manging unused switch ports
How to manage unused switch ports
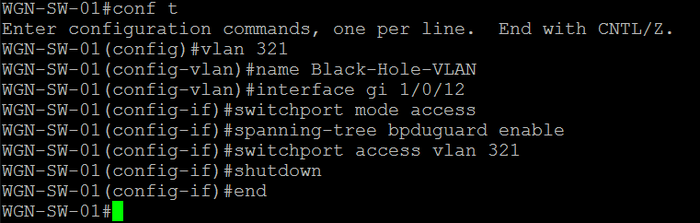
On networks I manage, I tend to simply shut down any unused access ports. Then when access is needed, I simply re-enable the port and assign it to the proper VLAN if needed. Some administrators take unused ports a step further by creating a black hole VLAN. This is a VLAN that's local to this switch only, has no layer 3 switch virtual interface (SVI) configured for it, and isn't allowed to traverse an uplink trunk port. Doing this guarantees isolation for any unauthorized devices connected to the switch port. This is especially useful if you are concerned about ports inadvertently being enabled when they should be disabled.
In this example, I assume that switch port 1/0/12 is a standard user port that is currently not used. First, I configure the black hole VLAN 321. Then I configure port 12 as an access port, enable BPDU guard, assign it to the black hole VLAN, and then disable the port by issuing the shutdown command:
page-4-image.png
Then once you need to activate the port, simply go back into switchport configuration mode, issue a no shutdown command, and assign it to the proper data and/or voice VLAN the user requires.
This guide was just a sample of the many access-port security configuration options available. Also note that there are more advanced, and purpose-built security tools for protecting network access such as Cisco ISE or ForeScout NAC. But if you don't have the budget for more advanced tools, you can at least get started by configuring the built-in security features on modern enterprise-class switches.
About the Author
You May Also Like




